28. October 2023
Tracer Fire CTF 2023

So what's Tracer Fire?
- "TracerFIRE (Forensic and Incident Response Exercise) for the U.S. Department of Energy (DOE) is a program developed by Sandia National Laboratories to educate and train cyber security incident responders (CSIRs) and analysts in critical skill areas. The program also aims to improve collaboration and teamwork among staff members. Under this program, several hundred CSIRs from the DOE, other U.S. government agencies, and critical infrastructure organizations have been trained." - acsac.org
Also, can't forget about Casey and Kevin: shoutout to them & Sandia National Lab for coming through to UNLV for their 2023 TracerFire CTF. While my team didn't place 1st for the CTF but got 1st for UNLV, it was still extremely enjoyable, as it really got me thinking of where I could improve when it comes to incident response and how we as a university could improve for future CTFs with an incident response theme or setup.
So how did we tackle on the CTF? With the mattermost channel we joined as a group I decided it would be best to have a central place for notes and progress on the CTF so I created a kanban board. From there we assigned each other categories in the CTF and helped each other out where needed. As for what I was able to solve(8 problems), I generally focused on the category regarding the ransomware. So let's dive in:
Davey Jone's Locker
- All Your File Are Belong to Us
- Prompt given: "On 10/20/2022, user mmilagro said they have a supicious pop-up on their screen asking for a ransom to unlock files as shown below:"
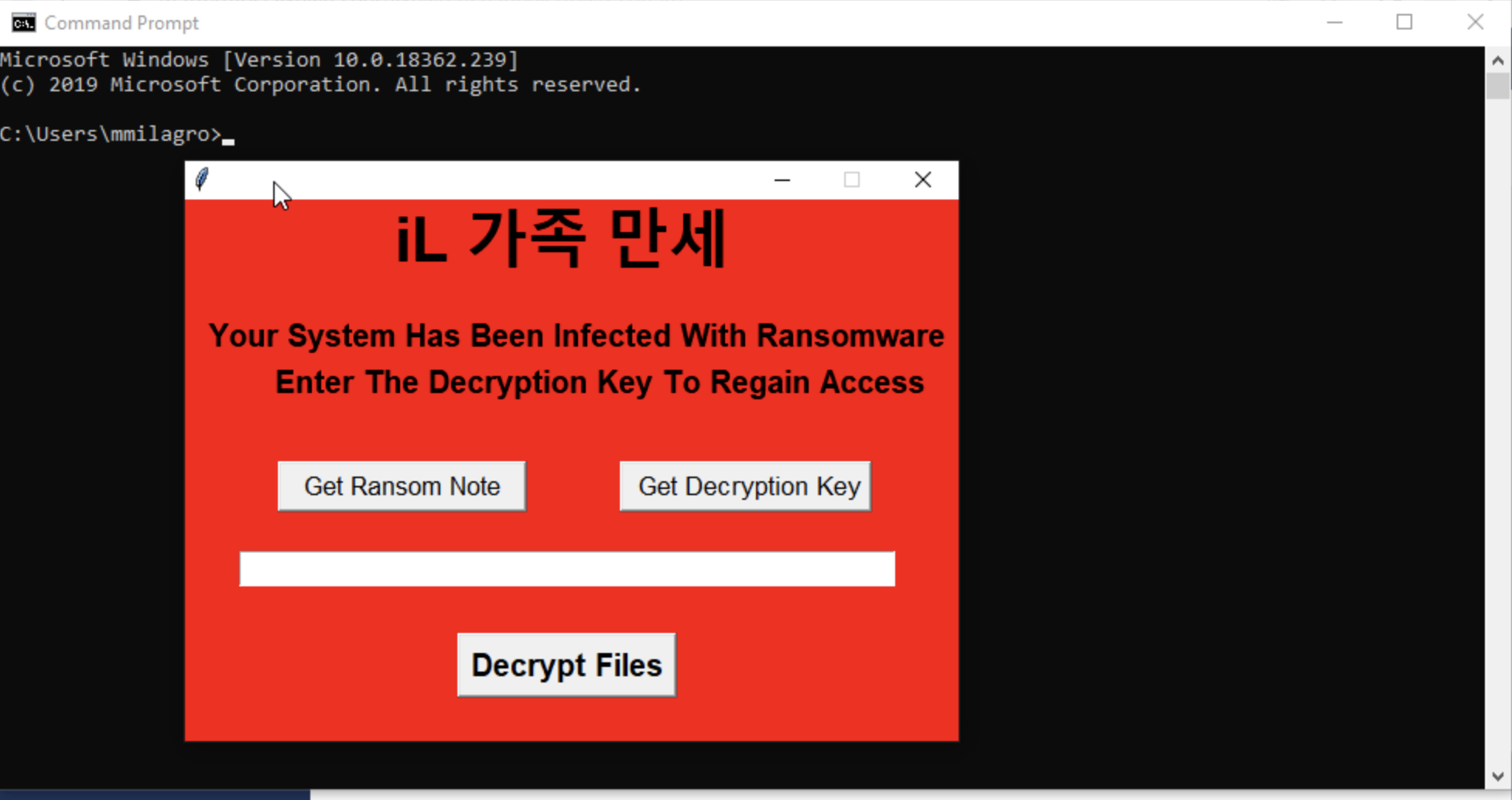
- "What process created this ransomware window?"
- So immediately my first thought was I don't see a title on the ransomware so there's no keywords to look for(previous strand of ransomware) but I do end up seeing the command prompt in the background. So my first thought is okay, let's narrow down the logs from just mmilagro and look for any instances of a command prompt being open. So I hop on the Elastic Stack and try to discover when command prompts were open and then after doing a text search for cmd.exe I narrow the time down to an hour after and before 15:07(The time cmd.exe was found) which is 14:00 - 16:00. From there I get stumped because even after narrowing down the logs to 2pm-4pm on the 20th from mmilagro's account there are still 35,000 events.
- So I keep thinking but after a while I decided to show my findings to the Sandia staff and get told to look at the ransomware icon and see where that leads me. Fortunately because of my previous experience with Python and Tkinter it immediately clicked that this was the default icon giving to Windows applications when developing with Tkinter. So with a text search of python, time range of 2pm-4pm on the 20th and logs only from the user.name mmilagro I was able to narrow down results to 14 hits. Immediately I saw the tkinter mentions as well as a call to hashlib so I knew this was related to the ransomware as hashlib was mostly likely used to encrypt the files. From these logs you would then find the proccess calling these resources was C:\Users\mmilagro\Downloads\SecurityUpdate.exe(15:07 first python call)
- Answer: SecurityUpdate.exe
- Process Created
- Prompt given: "What process created this ransomware executable?"
- Alright so we found the ransomware but now we got to think how did it get on the computer. Let's start with an Elastic search filtering down the event logs to only from mmilagro's account and a text search for securityupdate.exe with a 10 minute time range before 15:08(first python call made) on the 20th of October. This gives 1,208 hits but since we're interested in what created the executable we can sort just by time with earliest results showing first. The first result ends up being chrome.exe starting a file stream with the targetFileName being C:\Users\mmilagro\Downloads\SecurityUpdate.exe at 15:07:19.809. Boom so looks the ransomware was started through the browser.
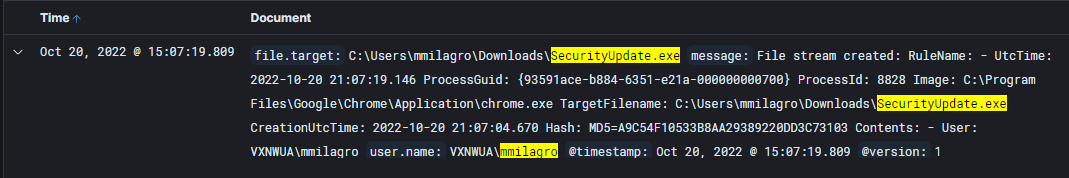
- Answer: chrome.exe
- Prompt given: "What process created this ransomware executable?"
- Domain Origin
- Prompt given: "What domain did this ransomware come from?"
- We knew the download started from chrome so now it's a matter of finding a dns query right before the download or finding the download link through the chrome log details. With our previous query narrowed down to only mentions of securityupdate.exe we can consider narrowing down the logs to only mentions of the "File stream" through the message field. After querying for that it gets narrowed down to 4 hits and we find one of the logs container a HostUrl value containing a link including securityupdate.exe (HostUrl=https://seokgasecuritysolutions.blob.core.windows.net/securityupdate/SecurityUpdate.exe)
- Answer: https://seokgasecuritysolutions.blob.core.windows.net (no defanging needed as URLs "should" be safe)
- Prompt given: "What domain did this ransomware come from?"
- Earliest User
- Prompt given: "Which user has the earliest creation of the ransomware file?"
- To find this I'm going to have to find everyone who downloaded the file at all. I'm going to assume that because one user uses chrome that there's a good chance everyone else probably does as well so we can filter for logs created specifically through chrome like the following photo shows. After filtering for that winlog.event_data.Contents value I get 3 hits with the following users: mmilagro, asarea & rblissitt. After ordering by timestamp I find out rblissitt was the first to download the ransomware at 15:02:19.616 on October 20th.
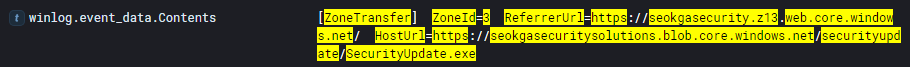
- Answer: rblissitt
- To find this I'm going to have to find everyone who downloaded the file at all. I'm going to assume that because one user uses chrome that there's a good chance everyone else probably does as well so we can filter for logs created specifically through chrome like the following photo shows. After filtering for that winlog.event_data.Contents value I get 3 hits with the following users: mmilagro, asarea & rblissitt. After ordering by timestamp I find out rblissitt was the first to download the ransomware at 15:02:19.616 on October 20th.
- Prompt given: "Which user has the earliest creation of the ransomware file?"
- URL Origin
- Prompt given: "Where did this malicious URL come from? Might want to check the browser or other applications the user was using."
- Let's try going through dns to see what's being accessed and limit it to events on the 20th before 15:03 (malware downloaded on rblissitt's computer) and events only from rblissitt's user account. This gives 44 hits and the last thing before the download was a dns query for pdat.matterlytics(related to mattermost), and before that was the dns query for the core.windows.net domains. So with the logs first pointing at mattermost and I decide to look for traffic pointing at mattermost and get into a rabbithole of logs not showing evidence of mattermost when there's a whole dns query saying something did happen.
- From here I decide to go wide and start fresh but looking at all the logs and slowly filtering out the noise. I start with user.name:rblissit and then filter registry noise as well as Windows applications found under process.executable. Then I filter to only logs including the process.executable field which ends up giving 9,168 hits with this query:
NOT process.executable: C\:\\Windows\\* AND process.executable: * AND user.name:rblissitt AND NOT event.dataset: "registry_create_delete"which funny enough the events given were all chrome so at this point I felt I wasted too much time and thought "I think at this point it's obvious chrome was being used so let's see what sort of history or crumbs Chrome leaves on the host". This leads to hopping on Velociraptor and checking out the rblissitt.vxnwua.net computer for any crumbs left by Chrome. In case you didn't know, you can find chrome history/files at a user's AppData\Local\Google\Chrome\User Data\Default\Sessions folder. 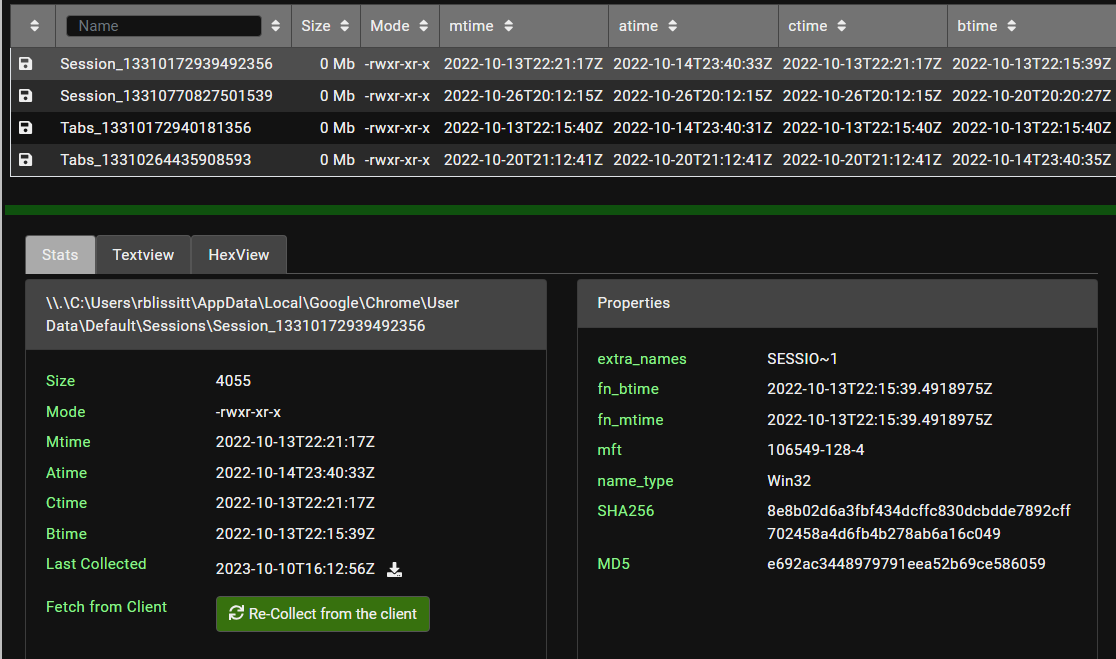
- Session_13310172939492356 ends up showing the user only opening new tabs so I move onto the next session. Session_13310770827501539 on the other hand had a TONN of links so first thing to do is Ctrl + F for my mattermost string and crazily enough we find a mattermost domain. With a bit more of Ctrl + F we end up finding the seokgasecurity domain right after some mattermost links so at this point this is enough confirmation for me.
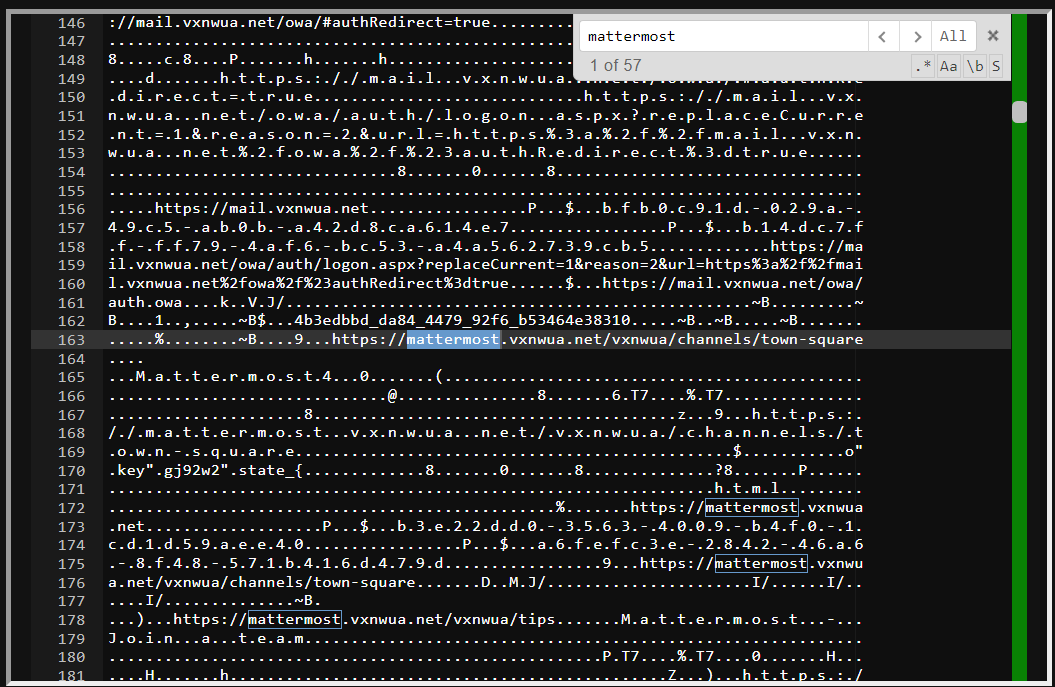
- Answer: mattermost
- Prompt given: "Where did this malicious URL come from? Might want to check the browser or other applications the user was using."
- Channel Name
- Prompt given: "What is the channel name of the Mattermost channel the users accessed?"
- With the previous research we just Ctrl + F for the mattermost domain of mattermost.vxnwua.net which and then look for a mention of channel in the link. There's 55 results that come up on the session file so to save some time let's do a regex string find of
mattermost\.vxnwua\.net.+channel. With this regex we end up finding 3 results showing https://mattermost.vxnwua.net/vxnwua/channels/town-square so looks like our channel is town-square - Answer: town-square
- With the previous research we just Ctrl + F for the mattermost domain of mattermost.vxnwua.net which and then look for a mention of channel in the link. There's 55 results that come up on the session file so to save some time let's do a regex string find of
- Prompt given: "What is the channel name of the Mattermost channel the users accessed?"
- Channel ID
- Prompt given: "What is the channel id for the Town Square Mattermost channel the users accessed?"
- Tried looking for this channel id with
[a-z0-9]{26}since I took a look into a couple channels I'm in with mattermost and they also seem to follow a number and letter combination with the id being 26 characters long. This led nowhere since I couldn't find IDs on rblissitt's machine sessions and the IDs I did find through Velociraptor on mmilagro's machine sessions weren't correct since the ID would have to be all machines not just one. From here I got stuck and decided to swap categories to try and get some more points
- Tried looking for this channel id with
- Prompt given: "What is the channel id for the Town Square Mattermost channel the users accessed?"
Pivoting to different category after getting stumped - Tidal Havoc
- Tidal Havoc 7
- Prompt given: "What time was this process created? Use the time in the timestamp field."
- First thing is first, let's read up on my partners' progress. Cool so looks like they found detected malware(alerts on ELK stack) on mmilagro's computer (192.168.125.14) which was reaching out to the ip 54.221.209.99 through an executable called businesslayer.exe which had a PID of 8012. Dope so let's filter our logs down with the information we have:
user.name: "mmilagro" and process.pid: 8012 and process.executable: "C:\\Program Files (x86)\\Businesslayer\\businesslayer.exe"and let's also sort these events with the earliest timestamp first. This gives the first log where the process got created and I find the timestamp to be Oct 16, 2022 @ 11:52:33.466 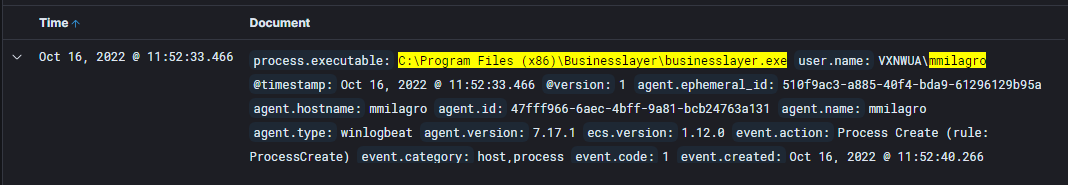
- Answer: Oct 16, 2022 @ 11:52:33.466
- First thing is first, let's read up on my partners' progress. Cool so looks like they found detected malware(alerts on ELK stack) on mmilagro's computer (192.168.125.14) which was reaching out to the ip 54.221.209.99 through an executable called businesslayer.exe which had a PID of 8012. Dope so let's filter our logs down with the information we have:
- Prompt given: "What time was this process created? Use the time in the timestamp field."
- Tidal Havoc 8
- Prompt given: "How many processes does businesslayer.exe create?"
- Now with only a couple minutes left in the competition I then try to rush through the filters to find something relating to the parent proccess. After some digging I find the process.parent.executable field and grab the full path of the businesslayer.exe file and create this query:
user.name: "mmilagro" and process.parent.executable: "C:\Program Files (x86)\Businesslayer\businesslayer.exe"which results in 6 hits. Unforunately as soon as the query gave the hits back the competition ended and I couldn't submit the anwser. 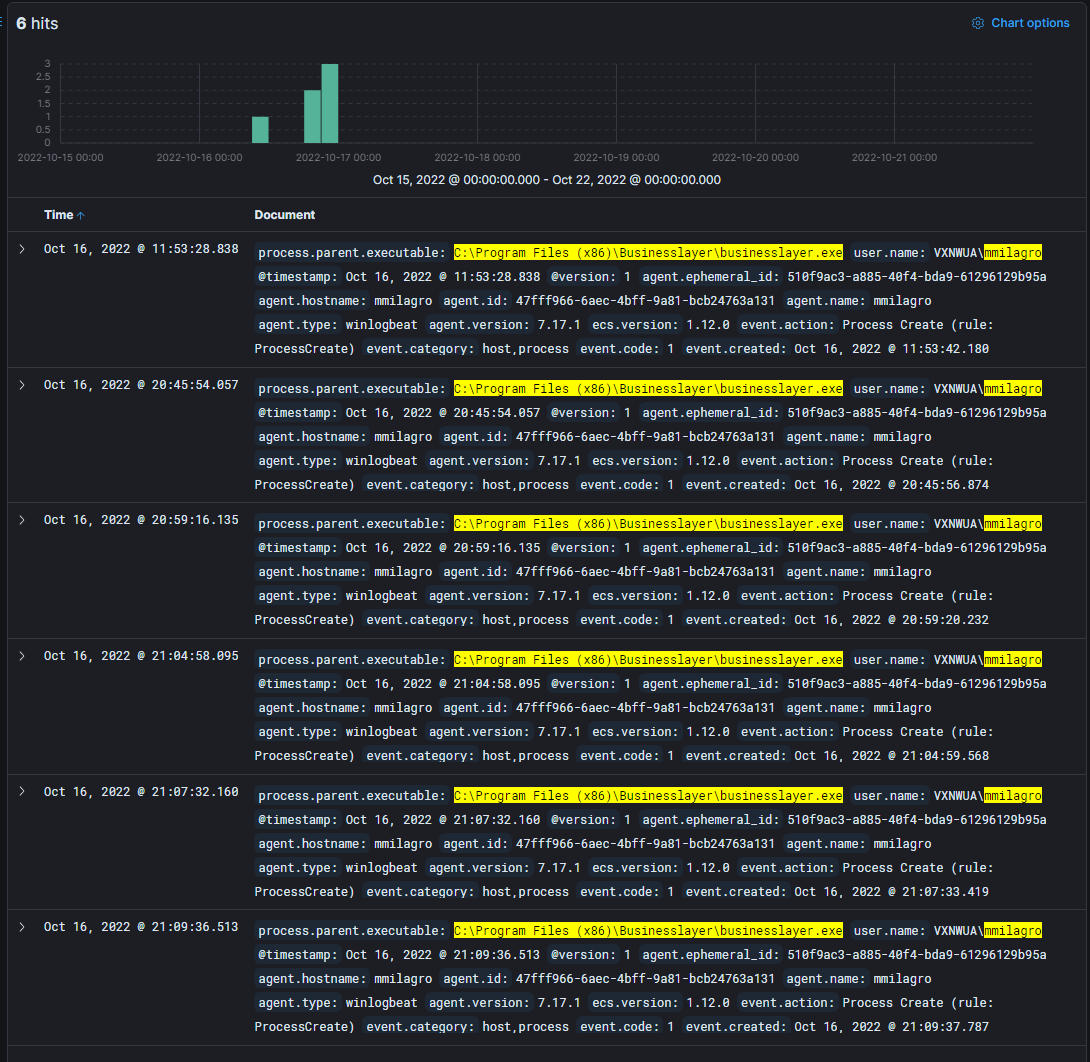
- Answer: 6
- Now with only a couple minutes left in the competition I then try to rush through the filters to find something relating to the parent proccess. After some digging I find the process.parent.executable field and grab the full path of the businesslayer.exe file and create this query:
- Prompt given: "How many processes does businesslayer.exe create?"
That's it, that is as far as I got in the 24 hour span of the competition on 10/21-10/22(did not stay awake through the night LOL) and I got to say: This was definitely one of the most enjoyable CTFs I done in a while. Shoutout to Man Vu for putting this together and having us students treated like royalty. Overall a great event and looking forward to the next TracerFire CTF!